Using your Home Router as a Secure Socket Proxy
f you use your Laptop computer at the local coffee shop, in a hotel while traveling, or at any location where you expect your online privacyat risk, you may want to consider some extra steps to protect your electronic mail and Web browsing behavior from those nosy prying eyes.
Using your computer in the above-mentioned places allows at least everyone with administrator-access to the local router to see what sites you visited. In case you aren’t reading your email through an SSL connection, it’s also not too hard to capture what you read and write; and no, it doesn’t matter if you use are using a Web browser or an email client application to access you email account.
However, if you have a hackable router at home and it is also accessible through a publicly routable IP address, you are in luck and with only a little time and effort, you can use your home-router as a secure proxy when you are on the road. The idea is to have your Laptop connect securely to your router at home; meaning, whenever your Laptop needs to request information from a resource on the Internet (DNS-Domain Name Service, HTTP-Websites, IMAP/POP3 Email, etc.) it encrypts the request and sends it to your router at home. The router decrypts the request, sends it on to the intended destination, and awaits the response. Eventually, the router will return the response to your Laptop, it is again encrypted, this time by the home-router, and decrypted on arrival at your Laptop. For those nosy prying eyes, all this will look like a long https connection, with undecipherable content. Sounds good? OK then let’s make it happen.
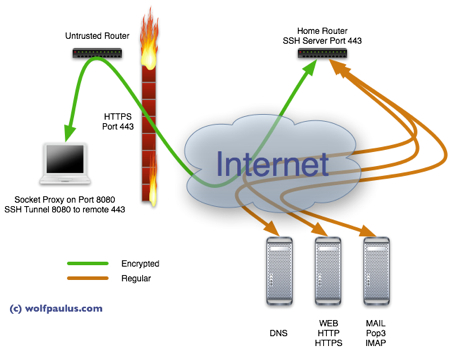
Let’s Get Started
As a 1st step, confirm that you have a hackable router. Make sure you it’s a Linksys WRT54G/GL/GS, Buffalo WHR-G54S/WHR-HP-G54, or other Broadcom-based routers. A details list of supported devices can be found here: http://wiki.openwrt.org/TableOfHardware?action=show&redirect=toh
There are several active and competing projects, all with the same goal, building a better, more powerful, and feature-rich firmware for your home router, I currently prefer the Tomato-Firmware, which is available for free at polarcloud.com. Following the detailed instructions provided with the Firmware distribution will replace the router’s original firmware with the Tomato firmware.
In case you are not the proud owner of a static IP address, you need to use a dynamic DNS (DDNS) service to create a hostname that points at all times to your dynamic IP. dyndns.com (https://www.dyndns.com/services/dns/dyndns/) allows you for free to do this and also provide an update mechanism, making the hostname work with a dynamic IP address. Dyndns will monitor your IP every 60s or every 4 hours, it’s your choice. The Tomato Firmware can also be setup to inform DynDNS whenever it detects an IP change. After doing this, your home router can always be reached by the name you picked, e.g. myrouter.homedns.org
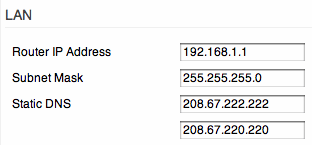
Not really necessary, but since it is a somewhat related topic, why not override the DNS entries your Internet service provider wants you to use and use opendns.org instead. Using OpenDNS, not only makes you independent from your providers DNS, it also has some cool features like Phishing Protection. Using OpenDNS is as easy as entering these two DNS addresses:208.67.220.220 and 208.67.222.222, under Basic/Network in the LAN Static DNS fields.
To make the new DNS settings immediately effective, you may have to reboot the computers attached to the router and also clear their browser caches and DNS caches. I.e., to clear the DNS cache in Leopard, open the terminal application and type the following command:dscacheutil -flushcache
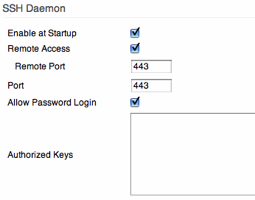
Enabling The SSH Daemon
As the final configuration step, the SSH daemon needs to be configured, which is done in the Administration/Admin Access area. Enable the daemon to start at startup and also enable remote access. The remote port is your choice; I have picked 443, to make access appear to be a regular, none suspicious https connection (see above). Further down on the configuration page a password needs to be set and confirmed. This password is later needed, when we want to establish a connection, when in the coffee shop or elsewhere.
Client Side / Mac OS X
Setting up the router was the hard part. From here on out it’s smooth sailing. On a Mac, there is nothing that needs to be installed. All we need to do is start an SSH Tunnel to the router and configure localhost as a socket proxy:
Starting the SSH Tunnel
Open a terminal and enter
ssh -ND 8080 -c blowfish -p 443 [email protected]
where myrouter.homedns.org is the name that you had registered with DynDNS and 8080 is the local endpoint into the tunnel. Instead of 3des, we use the faster blowfish encription protocol.
Making localhost a Socket Proxy
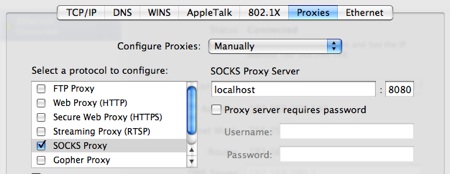
Open System Preferences / Network / Advanced and open the Proxies tab. Select SOCKS Proxy and enter localhost:8080 into the SOCKS Proxy Server field.
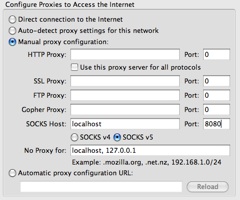
Alternatively, if you don’t want all traffic go through the tunnel but only traffic generated by Firefox, you don’t have to setup the general socket proxy but configure only Firefox instead. Open Firefox Preferences / Advanced / Network Settings and select Manual proxy configuration, enterlocalhost:8080 into the SOCKS Host field and select SOCKS v5.
Client Side / Windows
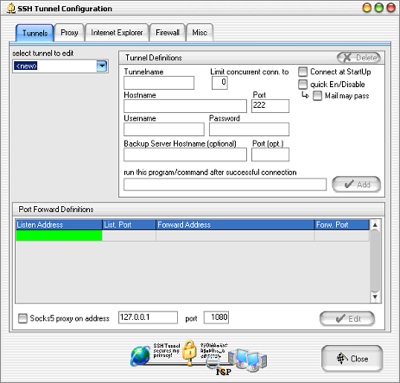
Since Windows does not come with SSH pre-installed. You would need to install an SSH client like PUTTY. For our purpose, rs4u’s SSH Tunnel seems to be the best client, which is available for free here: http://www.rs4u.com/SSHTunnel/
Again, after configuring and starting the tunnel, open Firefox Preferences / Advanced / Network Settings and select Manual proxy configuration, enterlocalhost:8080 into the SOCKS Host field and select SOCKS v5.
Done
That is it. All traffic to publicly routable addresses will now be encrypted and redirected through the tunnel, emerging unchanged on the other end, your home router. I know you have nothing to hide; but doesn’t it feel good to have a little more privacy? Anyway, get real. There is no privacy on the net! The traffic between your home router and your browsing destination is still unprotected and your ISP and everyone between him the destination still know exactly what you are up to.
.